today I went to my Online-Banking by typing in the correct domain name in Firefox. I could login and even see my actual balance. Then within the site a warning appeared that I should do a test-transfere for security reasons (over 7200€...). I didn't do this, but was wondering, because I still stayed on the original domain.
Checking the certificate showed me this (wrong, but valid. To compare with the original one: https://www.sparkasse-suedpfalz.de):
This type of certificate appears on every website I visit (inkluding stackexchange.com or google.com).: Instead of a certificate for [DOMAIN] i get one of *.[DOMAIN], where the CA is VeriSign.:
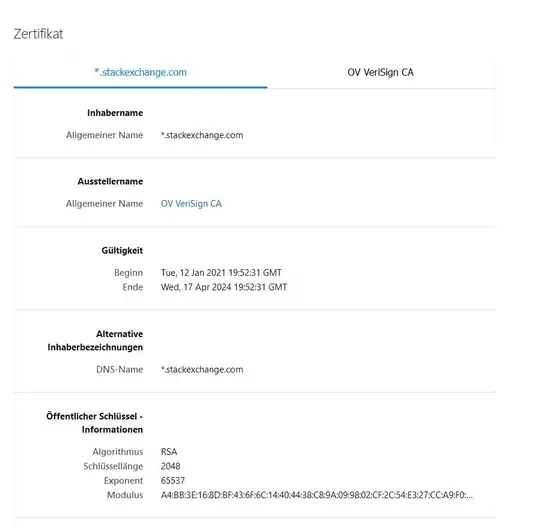
It happens with all browsers (Firefox, chrome, edge), but not with TOR. The OS is Windows 10 Pro, Version 10.0.19042 Build 19042
I dont have any issues on an other machines in the same intranet.
Are all requests from this computer send to a proxy? And how do they manage to insert fake requests to send money to the original domain? Happy if you have an idea what to do.
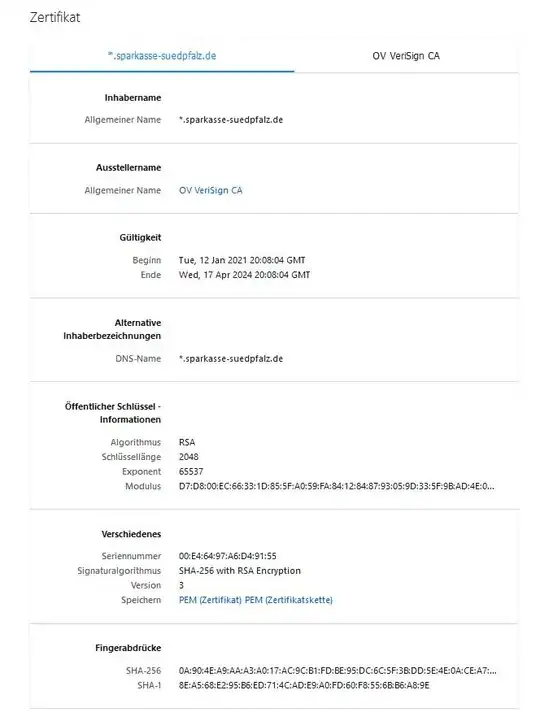
However, passwords shouldn't been stolen, since they are directly hashed, right? Of course I will change them anyway. My bank account is blocked allready.
– TheGermanGuy Jan 13 '22 at 22:50your browser <-TLS-> MITM server <-TLS-> actual site's server, where each<-TLS->is a separate TLS connection. So, the trip to the MITM's server could be more hops or less hops than the trip to the actual server. By any chance, are there any proxies set, or any changes to the network settings, in your browser's network settings or your system's network settings? – mti2935 Jan 13 '22 at 23:44